In the past, it was practical to block websites by examining simple HTTP headers (port 80). However, in today’s world, the transition of the vast majority of web traffic to the secure HTTPS protocol (port 443) and the emergence of advanced technologies have made traditional filtering methods seriously ineffective. Since HTTPS traffic is encrypted, it is practically impossible to inspect the requested content. This forces network administrators to use smarter techniques at lower layers or unencrypted variables such as SNI. That is why in this monovm article, we will examine how to use modern RouterOS capabilities to address these challenges.
Traditional Blocking Methods
This section examines two traditional methods that have been used to block website on mikrotik for years and analyzes their limitations in the face of modern encrypted traffic.
1. Blocking with MikroTik’s Internal Web Proxy (HTTP-Centric)
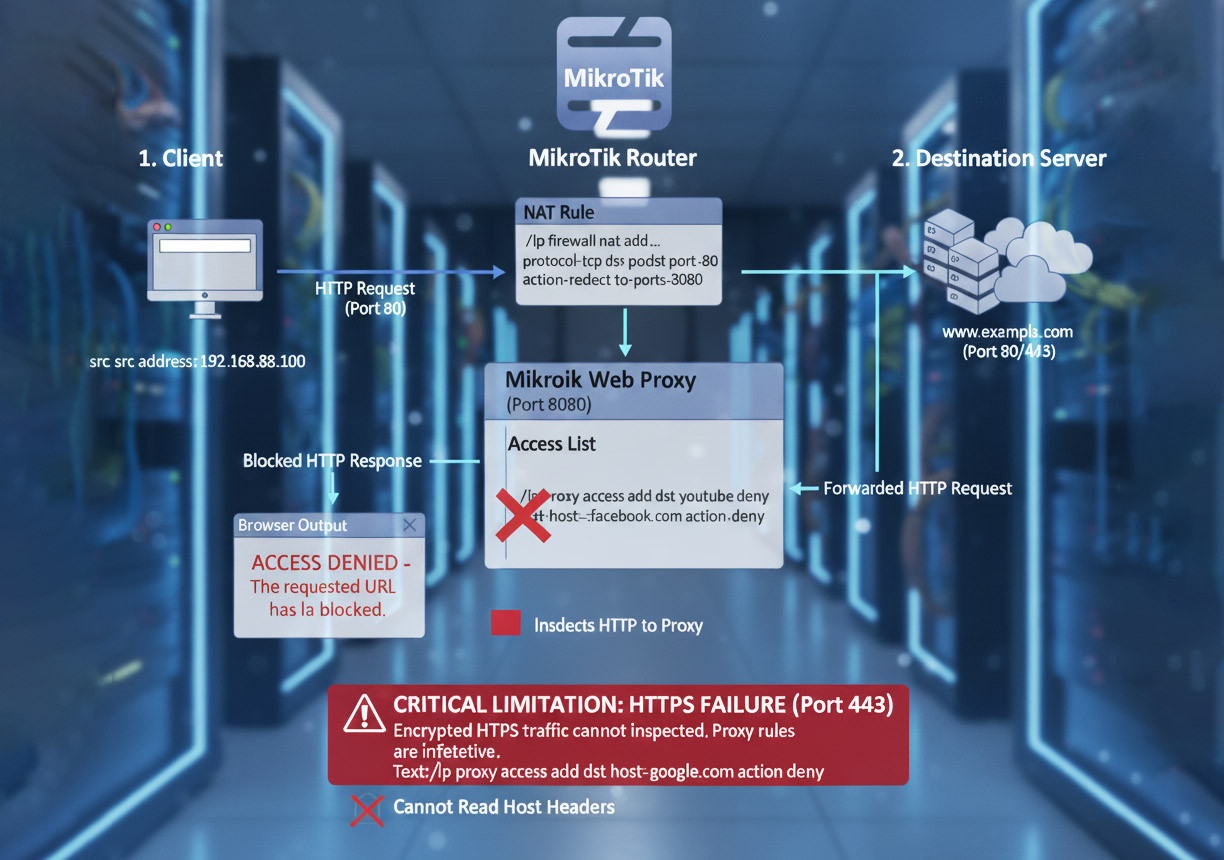
The MikroTik Web Proxy acts as an intermediary between the client and the destination server, capable of inspecting HTTP headers (Layer 7) before the traffic is forwarded to the destination. When functioning properly, this method provides a transparent and user-friendly output in which the user sees a clear “Access denied” message in their browser.
1.1. Implementing a Transparent Proxy
To use the proxy, the internal proxy service on the router must first be enabled and its port (usually 8080) configured. Next, a NAT rule must be created to redirect all HTTP traffic (port 80) from the internal network to the router’s internal proxy port:
/ip proxy set enabled=yes port=8080
/ip firewall nat add chain=dst-nat protocol=tcp dst-port=80 src-address=192.168.88.0/24 action=redirect to-ports=8080 comment="Redirect HTTP to Proxy"
1.2. Configuring the Access List
Actual blocking and mikrotik url filtering rules are defined under the ip proxy access menu. These rules use the dst-host variable to specify the destination domain name. To cover subdomains and multiple related domains, wildcards (*) can be used.
For example, blocking *.youtube.com will also block all YouTube subdomains.
1.3 Critical Limitation (HTTPS Failure)
Despite its simplicity, this method has a fundamental functional limitation in modern environments. The MikroTik Web Proxy, without complex SSL interception, cannot inspect HTTPS traffic (port 443).
Since the traffic is encrypted, the proxy cannot read host headers, rendering blocking rules ineffective. This means that MikroTik’s internal Web Proxy is practically unusable for content filtering today and can only manage unencrypted HTTP traffic.
This limitation has driven administrators toward firewall-based solutions instead.
2. Blocking with Layer 7 Protocols
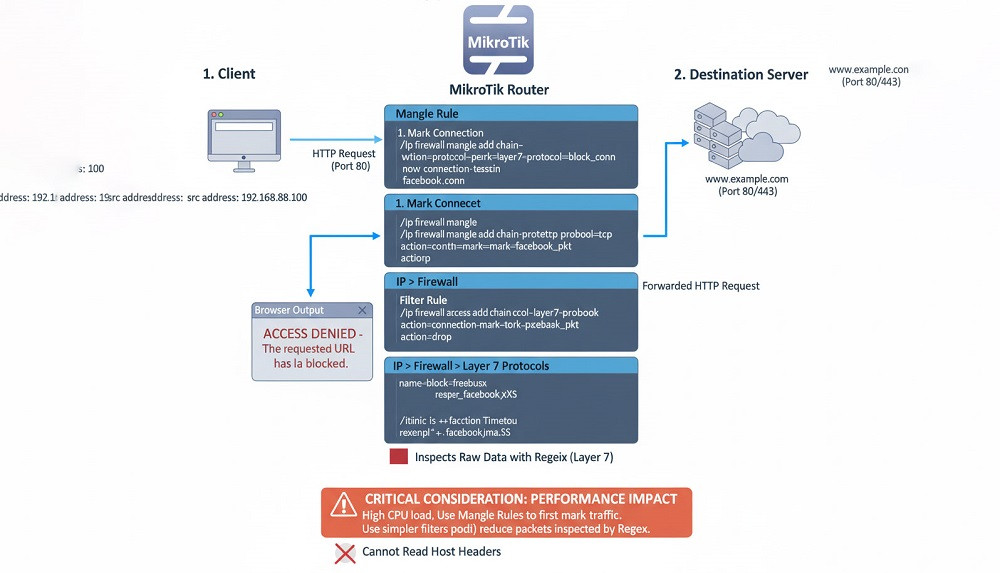
The Layer 7 (L7) protocol is a firewall feature that operates at the Application Layer of the OSI model. It uses regular expressions (Regex) to search for text patterns within the raw data of network packets in order to detect and block specific domain names or content.
2.1. Configuring Regex and Applying the Rule
To implement L7 filtering, the desired Regex pattern must first be defined under IP > Firewall > Layer 7 Protocols.
For example, the following pattern can be used to block Facebook:
/ip firewall layer7-protocol add name=block_facebook regexp="^.+(facebook).*\$"
Next, a filter rule is created in the forward chain to drop packets that match this pattern.
When this rule is applied, users will typically see a “Connection Timeout” or “This site can’t be reached” message in their browser.
2.2. Performance Issues and Technical Recommendations
The main drawback of the L7 method is that it imposes a very high CPU load on the router. To reduce this impact, the use of L7 must be done very carefully. A critical technical point is to first mark-connect the connection in question with L7, and then based on that mark, the packets are dropped using a roll filter (using Mangle Rules). It is also possible to use simpler filters (such as protocol and port) before referring to L7 to reduce the amount of data that needs to be Regex inspected.
Modern Filtering Methods
modern mikrotik url filtering methods are designed to be more efficient and lightweight, overcoming the challenge of HTTPS encryption.
1. Lightweight blocking with DNS Static (Blackholing)
.jpg?1762926931809)
This mikrotik dns blocking method operates at the name resolution layer instead of inspecting packet content and is very lightweight. In this mechanism the blocked domain name is intentionally pointed to an invalid IP address known as a blackhole such as 127.0.0.1 (IP loopback) or 0.0.0.0.
1.1. Implementing DNS Static
Configuration is done under IP > DNS > Static. Simply add a static record for the target domain:
/ip dns static add name=youtube.com address=127.0.0.1
/ip dns static add name=*.youtube.com address=127.0.0.1
The main advantage of this method is its very low consumption of router resources and its high speed. As a result, the user will see a message such as the site can’t be reached.
1.2. Critical drawback and the need to force DNS
mikrotik dns blocking method relies entirely on all clients in the network using the MikroTik DNS server. If a client can change its DNS settings to an external server such as 8.8.8.8 or use protocols like DoH, the DNS Static filter can be easily bypassed. Therefore, successful implementation of DNS Static requires firewall rules to force DNS traffic to the internal server which is discussed in section 5.
2. HTTPS Blocking with TLS-Host (SNI Matching)
.jpg?1762926906208)
Direct HTTPS blocking without decryption was a long-standing challenge until RouterOS v6.41 introduced the tls-host feature in the firewall, effectively solving this problem. TLS-Host uses the Server Name Indication (SNI) field, which is part of the TLS handshake process and contains the destination domain name in plain text. This allows the router to identify the domain name even within HTTPS traffic.
2.1. Implementing TLS-Host
The blocking rule is configured under IP > Firewall > Filter Rules in the forward chain. It should target TCP traffic on port 443 (HTTPS) and use a glob pattern in the tls-host field:
/ip firewall filter add chain=forward protocol=tcp dst-port=443 tls-host=*.facebook.com action=reject comment="Block Facebook via SNI"
block https sites mikrotik : It is recommended to use action=reject. Unlike drop, which silently discards packets, reject immediately terminates the connection and displays a “Connection Refused” message to the user, providing a better experience.
2.2. Modern Limitations
Despite its efficiency, TLS-Host has certain limitations. Its operation depends on receiving the complete initial TLS handshake frame without fragmentation; otherwise, the router may fail to detect the hostname. Additionally, new technologies such as ESNI (Encrypted SNI) encrypt the domain name itself, making hostname-based filtering a temporary solution.
3. Blocking with Address List (Only for Static IPs)
.jpg?1762926831505)
The Address List technique involves adding destination IP addresses to a firewall list, then blocking all incoming or outgoing traffic associated with that list. This method is lightweight and imposes minimal processing overhead.
However, Address Lists are ineffective for blocking large websites such as Facebook or YouTube, which rely on Content Delivery Networks (CDNs). The domains of such sites dynamically resolve to a vast number of changing IP addresses, making it practically impossible to track and update them all.
The optimal use of Address Lists is for blocking fixed internal servers or known IPs associated with attacks or filtering bypass methods (such as popular DoH servers). For a detailed guide on this method, check out our article on How to Block IP address in MikroTik.
4. Optimal Strategy: Combining Static DNS and TLS-Host
Performance analysis shows that using a single method alone is not enough, either due to the processing load (L7) or the vulnerability to bypass (Static DNS). The optimal strategy for URL filtering in MikroTik is a combination of Static DNS and TLS-Host. Static DNS, as the lightest method, reduces the initial processing load of blocking to close to zero. Then, TLS-Host acts as a deeper security layer in the firewall to ensure mandatory blocking of HTTPS traffic that is not blocked from local IPs. This combination provides an effective balance between network performance and security.
Comparison Table of URL Blocking Methods
For your better understanding of the aforementioned methods, a detailed comparison of the five main methods and the MikroTik combined blocking method (based on research findings on the RB750 router) is presented in the table below:
|
Feature |
Web Proxy (HTTP) |
Layer 7 Protocol |
DNS Static |
Firewall (TLS-Host) |
Hybrid Strategy (DNS Static + TLS-Host) |
|
HTTPS Support |
No |
No (ineffective) |
Yes (initial blocking) |
Yes (via SNI) |
Yes (complete and stable) |
|
CPU Load |
Medium |
Very High |
Very Low |
Low to Medium |
Low (optimized through DNS) |
|
Blocking Accuracy |
High (Hostname-based) |
High (Regex Pattern) |
Medium (Main Domain Only) |
High (TLS SNI) |
Very High (Combined DNS + TLS Host) |
|
User Output |
“Access Denied” |
“Connection Timeout” |
“Site Can’t Be Reached” |
“Connection Refused/Reset” |
Standard browser message or Timeout |
|
Main Weakness |
No HTTPS support |
Heavy CPU usage |
Requires local DNS enforcement |
Vulnerable to ESNI/Fragmentation |
Requires careful DNS–TLS coordination |
|
Best Use Case |
Small HTTP-based networks |
Experimental or selective filtering |
Lightweight initial blocking |
Advanced HTTPS filtering |
Modern HTTPS-heavy networks |
Studies show that the Layer 7 Protocol is not suitable for high-traffic networks due to its heavy CPU usage. In contrast, TLS-Host performs better for HTTPS filtering, while DNS Static offers lightweight and fast blocking. Combining the two in a Hybrid Strategy (DNS Static + TLS-Host) provides the best balance of performance, security, and filtering accuracy in MikroTik.
Best Practices for Network Administrators
To build a robust and efficient filtering strategy, it’s essential to follow these best practices:
- Prioritize firewall rules: Place blocking rules in the forward chain, after core rules like fasttrack-connection and accept established,related. This ensures legitimate traffic passes smoothly without adding unnecessary CPU load.
- Upgrade to RouterOS v6.41+ to benefit from SNI Matching and the tls-host feature for modern HTTPS filtering.
- Use a defensive combination (DNS Static + TLS-Host): As mentioned earlier, combining DNS Static for lightweight initial control with TLS-Host for deeper HTTPS inspection provides the most effective balance between speed and security.
- Optimize L7 with Address Lists: When Layer 7 filtering is required, first apply simpler filters like port or protocol, allowing only a small amount of data to reach Regex inspection. this significantly reduces CPU usage.
By applying these techniques together, you’ll achieve a seamless and high-performance URL blocking setup on your MikroTik router. For additional protection, you can also learn How to block port scanner in MikroTik.
Bypass Mitigation
A professional filtering architecture should include rules to prevent technical users from bypassing it. The two main bypass methods include using external DNS/DoH and tunneling through a VPN.
Blocking DNS over HTTPS (DoH) and Enforcing Internal DNS
To prevent DNS Static filters from being bypassed, implement the following:
1. Force clients to use the router DNS (port 53 redirect):
All standard DNS requests (UDP/TCP port 53) leaving the internal network should be redirected to the MikroTik router’s IP. This ensures that even if a client configures an external DNS, it will still use the router:
/ip firewall nat add chain=dst-nat protocol=udp dst-port=53 action=dst-nat to-addresses=<Router-IP> to-ports=53 comment="Force internal DNS (UDP)"
/ip firewall nat add chain=dst-nat protocol=tcp dst-port=53 action=dst-nat to-addresses=<Router-IP> to-ports=53 comment="Force internal DNS (TCP)"
2. Block DoT ports and ping checks
DNS over TLS (DoT) uses port 853, which should be blocked:
/ip firewall filter add chain=forward protocol=tcp dst-port=853 action=drop comment="Block DoT"
/ip firewall filter add chain=forward protocol=udp dst-port=853 action=drop comment="Block DoT"
3. Identify and block DoH server Ips
DoH traffic uses the same HTTPS port (443), but you can mitigate it by creating an Address List of known DoH servers (e.g., 8.8.8.8 and 1.1.1.1) and applying a reject rule instead of drop. ICMP should not be blocked so devices don’t mistakenly consider the internet unreachable:
/ip firewall filter add action=reject chain=forward dst-address-list=public-resolvers protocol=!icmp reject-with=icmp-protocol-unreachable comment="Block DoH IPs except PING"
Combining port 53 redirection with selective blocking of popular DoH IPs provides the most practical defense within MikroTik’s standard capabilities.
2. Preventing Tunneling and VPN Bypass
To stop unauthorized VPNs that bypass web filters, core tunneling protocols should be dropped in the forward chain:
|
Protocol |
Type |
Port / ID |
Sample Firewall Rule |
|
IPIP |
IP Protocol ID 4 |
– |
/ip firewall filter add action=drop chain=forward protocol=ipip comment="Block IPIP Tunnels" |
|
GRE (PPTP) |
IP Protocol ID 47 |
– |
/ip firewall filter add action=drop chain=forward protocol=gre comment="Block GRE Tunnels" |
|
IPSec ESP |
IP Protocol ID 50 |
– |
/ip firewall filter add action=drop chain=forward protocol=ipsec-esp comment="Block IPSec ESP" |
|
PPTP |
TCP |
1723 |
/ip firewall filter add action=drop chain=forward dst-port=1723 protocol=tcp comment="Block PPTP Control" |
|
L2TP/IPSec |
UDP |
500, 1701, 4500 |
/ip firewall filter add action=drop chain=forward dst-port=500,1701,4500 protocol=udp comment="Block IKE/L2TP Ports" |
This version keeps all essential code and operational notes while making the text smoother and slightly more concise without removing critical content.
Troubleshooting and Performance Monitoring
Implementing firewall rules, especially in large networks, requires continuous monitoring and precise troubleshooting.
Safe Testing and Rule Monitoring
When applying significant changes, particularly Drop or Reject rules, use Safe Mode in WinBox to ensure that any errors automatically revert the changes and maintain router access.
To verify rule effectiveness, use /ip firewall filter print stats to see the number of packets and bytes blocked by a specific rule. A zero count indicates that the rule is not matching traffic correctly.
Connection Analysis and CPU Load Management
The IP > Firewall > Connections menu shows the status of connections (Established, Related, Invalid), with invalid connections potentially indicating unauthorized traffic or intrusion attempts.
When using Layer 7, regularly monitor CPU usage; sudden spikes, especially under high traffic, signal the need to migrate to lighter solutions like TLS-Host. Enabling fasttrack-connection in RouterOS v7 for authorized connections reduces CPU load and improves overall network performance.
The Smart Way Forward
As you’ve seen, building a professional and stable filtering system for your network requires finding the right balance between performance, accuracy, and security. That’s why we recommend using hybrid filtering methods to achieve the best results.
Finally, if you want to implement these solutions in a powerful and always-available environment, we recommend using our MikroTik server. This service gives you full control, high scalability, and advanced management tools, allowing you to build a secure and professional filtering system for your network.
People are also reading:
![How to Block Websites on MikroTik Router [Multiple Methods Explained]](/wp-content/uploads/2020/09/133930-main.webp)
I’m Oliver k. I have MS degree in Computer Engineering. For nearly 5 years that I have been working on web programing and also in last 2 years I have worked on windows and Linux VPS. This is my honor to share my experiences with a new community.