List of content you will read in this article:
In the ever-evolving landscape of network security, safeguarding your MikroTik router against unauthorized port scanning is paramount. Port scanners, tools used to identify open ports and vulnerabilities in network devices, can be a prelude to more sophisticated cyber attacks. This guide delves into the effective strategies to block port scanners on your MikroTik device, ensuring robust security and peace of mind. We will explore step-by-step methods to configure firewall rules, employ port-knocking techniques, and leverage MikroTik's advanced features to fortify your network against these intrusive scans.
How to Block Port Scanner and Prevent It in Mikrotik?
Some applications or sites can scan your MikroTik sever and gain detailed reports about the ports in use (or free). To avoid these reports, we should know those IPs and block them. Follow the steps below to add specific regulations to drop these connections.
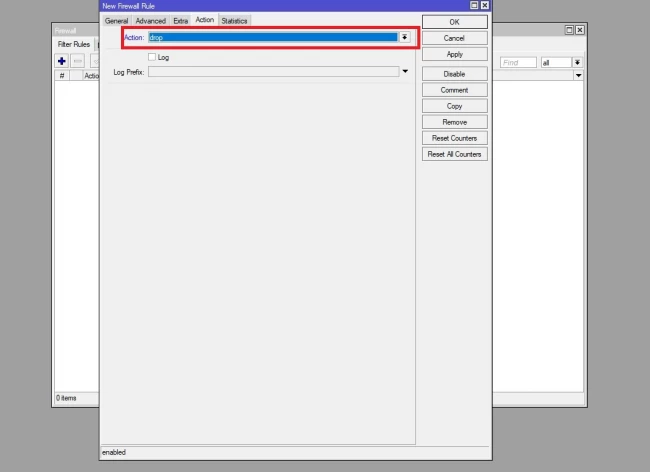
- First, we should know what type of connections are used for scanning. For this, we add a rule to detect the IPs. Open IP> firewall select the “filter rules” tab and click on “+”. In the opened window select chain as “input” and for protocol type, set to “6(TCP)”. Switch to the action tab and select the action method to “add src to address list”. Then enter a name for the address list field or select from the available.
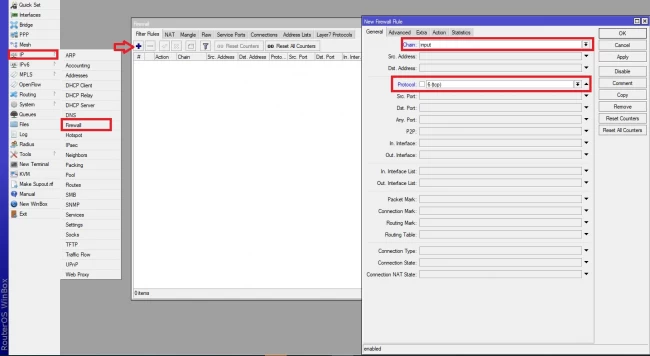
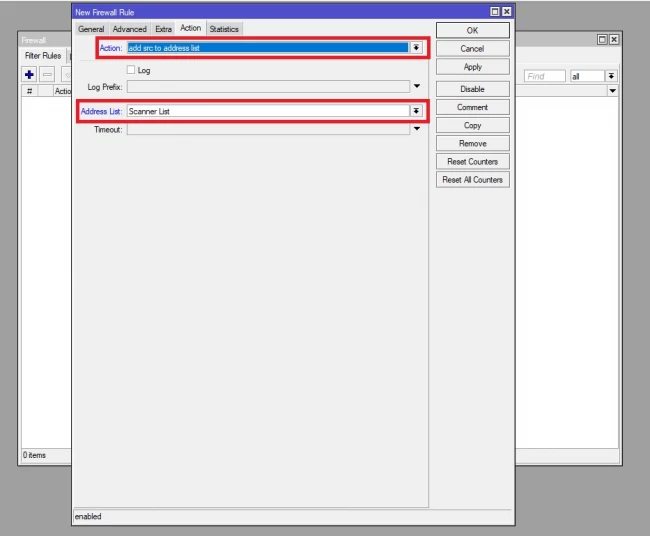
- In the step above we learned to add port scanners, IPs to the list. In this step, we should drop all these IPs. To do this action, click on IP>firewall, and in the filter rules tab, click on “+” icon. Select chain as input and go to the advanced tab. select your IP list name in the “Src. Address List” and at the end click on the action tab and select action as a drop.
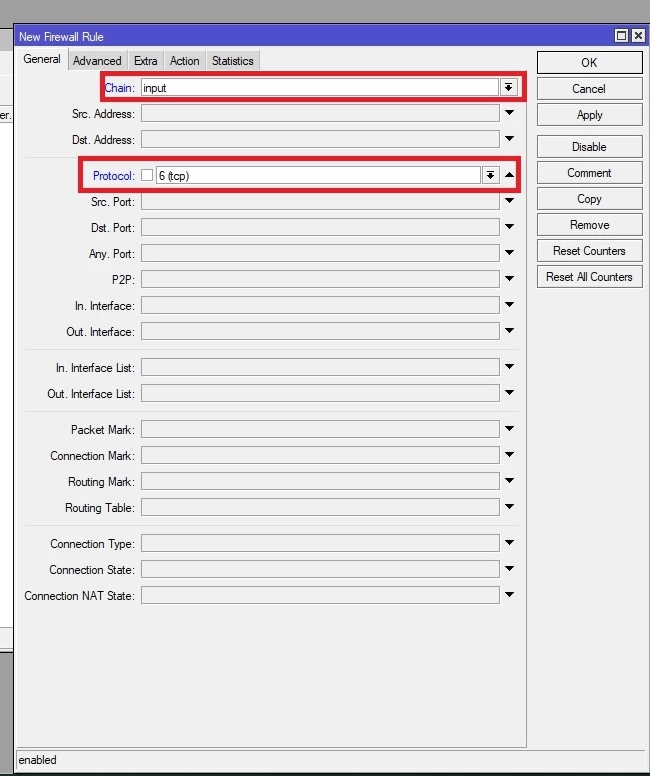
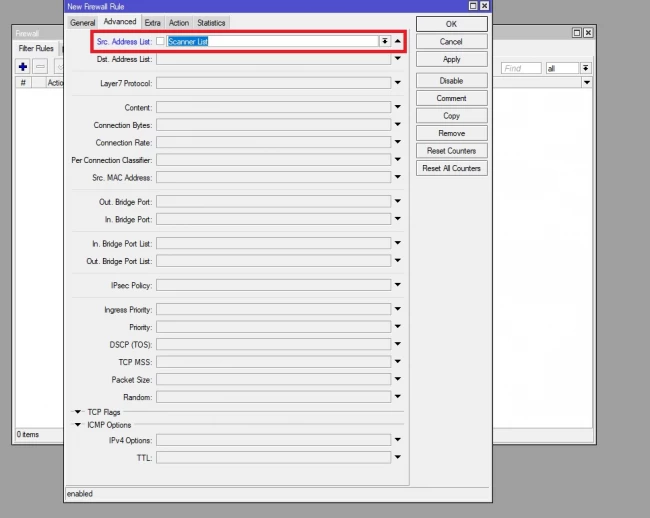
Conclusion
In conclusion, securing your MikroTik router from port scanners is a critical step in fortifying your network's defenses. By implementing the techniques discussed in this guide, such as configuring firewall rules and using advanced features of MikroTik, you can significantly enhance your network's security posture. Remember, the key to effective network security is continual vigilance and adaptation to new threats. With your MikroTik router now better guarded against port scans, you can have greater confidence in the integrity and safety of your network infrastructure.
![How to block port scanner in MikroTik [Prevent Port Scanning]](/wp-content/uploads/2020/09/146520-main.webp)
I’m Oliver k. I have MS degree in Computer Engineering. For nearly 5 years that I have been working on web programing and also in last 2 years I have worked on windows and Linux VPS. This is my honor to share my experiences with a new community.