List of content you will read in this article:
In the realm of open-source operating systems, Linux shines as a symbol of adaptability and innovation. Among its many distributions, one stands out for its mystical allure - Kali Linux. Named after the formidable Hindu goddess of destruction and transformation, Kali, this specialized operating system is a favorite among ethical hackers and cybersecurity experts.
In this comprehensive article, we delve into the world of Kali Linux, unearthing its origins, highlighting its robust features, and showcasing its undeniable advantages. We will unravel the secrets of Kali Linux, uncovering its unparalleled potential as the ultimate cybersecurity toolkit.
Whether you're an enthusiast or a seasoned professional, get ready for an enthralling journey into the world of Kali Linux. Let's unleash the power of this cyber-sorcery together!
What is Kali Linux?
Kali Linux traces its lineage back to the revered BackTrack Linux, a popular penetration testing distribution used by cybersecurity enthusiasts and professionals. After critically reviewing and refining over 600 penetration testing tools from BackTrack, the creators of Kali Linux eliminated redundant or malfunctioning tools, resulting in a leaner and more efficient toolkit.
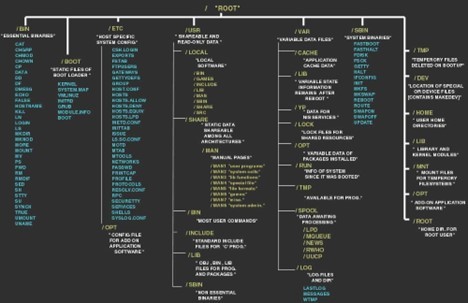
Since its inception, Kali Linux has remained committed to the principles of open-source development. The entire development tree, including the source code of every package, is made available to the public, enabling users to customize and adapt the system according to their specific needs. Furthermore, Kali Linux adheres to the Filesystem Hierarchy Standard (FHS), ensuring a consistent and easily navigable structure for Linux users.
Features of Kali Linux
Kali Linux stands as the ultimate cybersecurity toolkit, designed to empower professionals in the realm of security assessments. With a comprehensive arsenal of cutting-edge tools, Kali Linux offers unmatched potency, comprising a vast array of penetration testing resources.
It remains forever free and open-source, adhering to the principles of transparency and collaboration.
With extensive wireless device support and a custom kernel optimized for wireless injection, it enables seamless and thorough wireless assessments. Developed in a secure environment and backed by GPG signed packages, Kali Linux ensures integrity and authenticity.
Multilingual support, complete customization options, and compatibility with ARM devices further enhance its appeal.
In essence, Kali Linux is the go-to solution for cybersecurity experts, providing a versatile and powerful platform for safeguarding networks and identifying vulnerabilities.
Why Use Kali Linux?
Kali Linux stands out as a powerful and preferred operating system for various reasons. First and foremost, its perpetual free availability makes it an attractive choice for users seeking a reliable and cost-effective solution. The fact that Kali Linux remains free for life ensures accessibility and removes any financial barriers.
Another compelling reason to use Kali Linux is the vast array of specialized tools it offers. With over 600 unique tools dedicated to security analysis and penetration testing, Kali provides a comprehensive toolkit for cybersecurity professionals and ethical hackers.
This wealth of tools empowers users to identify vulnerabilities, assess system weaknesses, and enhance overall security measures effectively.
Moreover, Kali Linux's open-source nature adds to its allure. Much like the appeal of Android OS over iOS for those who appreciate customization and control, Kali Linux adheres to the open-source philosophy.
This not only fosters a collaborative and supportive community but also enables developers and users to tweak and modify the OS as per their specific needs and preferences.
Additionally, Kali Linux embraces multi-lingual support, encouraging individuals from diverse backgrounds to come together and utilize the tools it offers for achieving their unique goals.
This feature-rich and adaptable OS has rightfully earned its reputation as a leading choice for those focused on cybersecurity and ethical hacking endeavors.
Uses of Kali Linux
Kali Linux stands at the forefront of advanced-level Security Auditing and Penetration Testing, catering to a wide range of cybersecurity tasks, including information security, security research, penetration testing, reverse engineering, and computer forensics.
To unlock the full potential of Kali Linux, professionals must adhere to a series of crucial steps for proper installation. This comprehensive guide delves into the world's most revered OS, offering invaluable insights into its multifaceted uses.
Before venturing further, users gain a clear understanding of why Kali Linux proves indispensable, despite several other commercial computer OS options. It's vital to note that each version of Kali Linux boasts unique package types, warranting careful consideration during the installation process.
1. Installing Git
To access and download sample codes from any git repository, you need to install Git. This step is often referred to as cloning a repository and requires the use of a git command. To proceed with the installation, simply write "apt install git" to address the necessary dependencies in the OS. The image below provides a visual guide for a clearer understanding. Once Git is installed, you can effortlessly visit a GitHub repository, select your desired content from the list, and begin exploring and utilizing the code.
2. Installing TOR
Installing TOR is a crucial step in Kali Linux to enhance privacy and protect against DDoS attacks. TOR's anti-censorship features act as a shield against potential hackers and make it an attractive target for anyone seeking to develop exploits.
Before proceeding with the installation, it is essential to check the Kali repository for the latest version of TOR. Once installed, regularly updating TOR will address a significant portion of potential issues, making your overall experience more secure and reliable.
3. Installing Terminal Multiplexer
To enable the installation of several scripts from a single terminal window, you can install a Terminal Multiplexer. This allows users to switch between different tasks seamlessly using various tabs within the terminal.
The installation process for the Terminal Multiplexer, known as "Tilix," is straightforward. Simply type the command "apt install tilix" in the terminal, and the installation process will begin. Once the installation is complete, users can access Tilix by typing "Tilix" in the terminal.
With Tilix, managing multiple tasks becomes more efficient, as it streamlines the execution of various scripts and commands from a unified terminal interface.
4. Configuring Bash Aliases
To ensure a smooth installation of software packages, it is essential to update and upgrade the computer regularly. This process should be done frequently to keep the system up-to-date and avoid compatibility issues.
Bash Aliases play a significant role in this process, as they allow users to create shortcuts for commands or customize the terminal environment according to their preferences. These aliases are saved in a file that users can access and modify. To update Bash Aliases, users need to type "nano -/.bash_aliases" in the terminal and press enter.
This action will open a list of distinctive aliases, which can be edited or expanded to suit individual needs and streamline command usage for enhanced productivity.
5. Setting Up New Low-Privileged User
Creating a new low-privileged user is essential to enhance security by reducing the risk of unauthorized access and potential attacks. By limiting the user's privileges, it minimizes the impact of potential breaches on the system.
In Kali Linux, adding a low-privileged user is a straightforward process. The command to achieve this is "Add user {name of the user account}". After entering the command, you'll be prompted to set a new password and provide additional information like Room Number, Home Phone, and Work Phone for user identification.
Once the data is entered, you'll need to confirm that the inputs are correct, completing the setup of the low-privileged user account. This user account ensures that critical software components running with elevated privileges cannot be easily compromised, enhancing the overall security of the system.
6. Install Hacking Tools
Upon completing the installation of Kali Linux, you may notice that it does not come pre-loaded with all the necessary tools. To streamline the process of installing tools individually, you can use the following command:
"Sudo apt update && Sudo apt install and the name of the said data package."
By executing this command, you can easily update the package list and then proceed to install the desired tools in a more convenient and efficient manner. This approach saves you the hassle of installing each tool one by one, allowing you to quickly equip Kali Linux with the essential tools needed for your specific tasks.
Top Tools in Kali Linux
- John the Reaper - John the Ripper is a versatile open-source password recovery tool that caters to all operating systems and distributions. You have two options for obtaining it: either download the source code and compile it manually, or opt for a release package specifically tailored for your system or distribution.
This flexibility ensures that users can seamlessly integrate John the Ripper into their preferred environment to efficiently recover passwords and strengthen their security measures.
- Metasploit - Kali Linux offers a comprehensive suite of built-in tools, specifically designed for penetration testing purposes. Among these tools, the Metasploit framework stands out, empowering red teamers to conduct effective reconnaissance, scanning, enumeration, and vulnerability exploitation across various applications, networks, servers, operating systems, and platforms.
While its primary focus revolves around pre- and post-exploitation tasks in penetration testing, Metasploit also proves invaluable for exploit development and vulnerability research. This powerful framework equips security professionals with the capabilities needed to identify and address potential weaknesses.
- Netcat - Netcat, a versatile network utility tool, serves as a valuable asset for reading and writing data on network connections. This lightweight and straightforward application finds practical use in command lines for various scenarios. Operating over both TCP and UDP protocols, Netcat is designed to seamlessly integrate into other programs.
This feature makes it ideal for incorporating a few lines of Netcat code into pentesting scripts, enhancing their capabilities and facilitating network-related tasks. Its flexibility and ease of use make Netcat an indispensable tool for security professionals and enthusiasts seeking efficient network communication and testing solutions.
Advantages of Kali Linux
Kali Linux offers a plethora of compelling features that make it a go-to choice for network security teams and penetration testers. Here are some notable features:
- Extensive Toolset: Kali Linux houses more than 600 penetration-testing tools, catering to various aspects of network security assessment. This extensive toolset ensures comprehensive coverage and leaves no room for oversight. Security professionals can choose from a wide array of tools to perform tasks like vulnerability scanning, password cracking, and wireless network analysis, providing them with the flexibility needed to address diverse security challenges effectively.
- File-System Hierarchy Standard: Kali Linux adheres to the Filesystem Hierarchy Standard, simplifying tool accessibility. Users can easily locate support files, binaries, and libraries without manual searches, enhancing overall usability. This adherence to standards not only streamlines navigation but also facilitates seamless integration with existing infrastructure, making it easier for security teams to incorporate Kali Linux into their workflow.
- Open Development Tree: Kali Linux's open-source nature allows users to inspect and access the system's code freely. This transparency fosters community involvement, enabling users to contribute to its development and security enhancements. Moreover, it provides insight into the development process, ensuring that the system's integrity is maintained and potential vulnerabilities are quickly identified and addressed.

- Multiple Language Support: Despite most penetration tools being in English, Kali Linux offers complete multilingual support, accommodating users who prefer to work in their native languages. This inclusivity fosters a global community of security professionals who can access and utilize Kali Linux in a language they are most comfortable with, promoting effective collaboration and knowledge sharing among diverse teams.
- Customizability: Kali Linux is highly customizable to suit the specific requirements of security professionals. The meta packages and ISO customization process facilitate the creation of tailored versions of the OS. This level of customization allows security teams to build specialized Kali Linux distributions tailored to their unique needs, ensuring that they have the exact tools and configurations required for their projects.
- Free and Always Will Be: Kali Linux, like its predecessor BackTrack, is entirely free and will remain so. Users can access its powerful tools without any cost, removing financial barriers and ensuring that anyone, regardless of their budget, can leverage its capabilities for security testing and network assessments. This affordability democratizes the field of cybersecurity and encourages learning and skill development.
- Wide-Ranging Wireless Device Support: Kali Linux addresses the common challenge of wireless device support in Linux distributions. It offers comprehensive support for various wireless devices, allowing seamless connectivity to USB and other wireless devices. This extensive support ensures that security professionals can work with a wide range of hardware, including wireless network cards and USB adapters, ensuring compatibility with the latest technologies and making it easier to perform wireless security assessments.

Why Ethical Hackers Use Kali Linux?
Kali Linux is the most favorite and sought-after OS for ethical hackers and other cyber professionals. There are several reasons behind it. The entire source code of Kali Linux is open-sourced. This allows cybersecurity experts and analysts to tweak the operating system based on their requirements. Moreover, it has more than 600 tools for penetration testing that comes pre-installed with it which makes it the swiss-knife of ethical hackers. Some of the most popular tools are Nmap, Metasploit, Armitage, Wireshark, OWASP ZAP, John the Ripper, Aircrack-ng, etc.
