List of content you will read in this article:
When installing Kali Linux on Windows, there could be problems that arise. One such problem that users will encounter is the problem with installing Kali's packages. Windows defender prevents from running and even install them at some points. Sometimes, when you want to install some Kali packages, Windows Defender will identify it as malware and will prevent it from installing and running.
What is Kali Linux?
Kali Linux is, as you might have guessed, is a Linux distribution, to be more specific, is Debian-based. Unlike the other distributions on the market, however, it has a very specialized purpose. It was developed for use by penetration testers, IT security professionals, and digital forensics specialists.
Considering its designed purpose, Kali Linux comes with a plethora of pre-installed tools which are used for a wide range of cybersecurity-related tasks. In fact, there are over 600 tools included within Kali Linux that can be used for penetration testing and cybersecurity purposes. If you wish to get into the field of cybersecurity, knowing your way around Kali Linux is a must. Here is a guide on how to install Kali Linux in windows from the Microsoft store so that you can get started straight away.
Features of Kali Linux
There are many attractive features to look forward to within Kali Linux, especially when concerning IT security and penetration testing. Here are some of them:
600+ Pre-installed Penetration Tools
Kali Linux has over 600 useful pen-testing tools such as:
- Aircrack-ng: A tool for intercepting and breaking passwords in wireless communications
- Burp Suite: A tool to penetrate web-based systems that use the HTTP protocol
- Wireshark: A tool for analyzing packets in network protocols
Developed within a Secure Environment
While Kali Linux itself is open-source, with its development tree available for viewing to the general public, the code repositories are, in fact very secure. The Kali Linux team is made up of a small group of individuals who are the only ones trusted to commit packages and interact with the repositories, all of which is done using multiple secure protocols.
Adheres to FHS Standard
To summarize, the Filesystem Hierarchy Standard (FHS) enables software to predict the location of installed files and directories and users to predict the locations of installed files and directories. This is done by specifying guiding principles for each area of the filesystem, specifying the minimum files and directories required, enumerating exceptions to the principles, and Enumerating specific cases where there has been historical conflict.
Who is it for?
Kali Linux is quite a unique operating system. Not only is it used by IT professionals, but it also is a popular platform amongst black hat hackers. Except for that unfortunate fact, here are a few groups of people that use Kali Linux:
- Network Architects: these professionals are responsible for designing secure network environments. They use Kali Linux to test their original designs to make sure no security flaw was overlooked or improperly configured.
- Network Administrators: while network architects design the networks, network admins maintain it and make sure it is efficient and secure. With the help of Kali Linux, they can audit the network.
- Security Administrators: they also utilize Kali Linux to ensure that there are no easily discoverable vulnerabilities.
- Penetration Testers: The group of users that the OS was originally designed for; use Kali Linux to perform reconnaissance and audit corporate environments they were hired to review.
- Forensic Engineers: Kali Linux possesses a “Forensic Mode”, which allows a forensic engineer to perform data discovery and recovery in some instances.
- Computer Enthusiasts: while “computer enthusiast” is a pretty generic term, anyone interested in learning more about networking or computers, in general, can use Kali Linux to learn more about Information Technology, networking, and common vulnerabilities.
How to Fix Kali Linux Packages not Installing
Follow this guide in order to fix this issue:
Step 1: Open Kali Linux through CMD or the start menu.
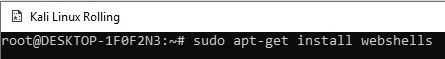
Step 2: Now by entering the webshells command, Windows Defender will display security problems.
sudo apt-get install webshells
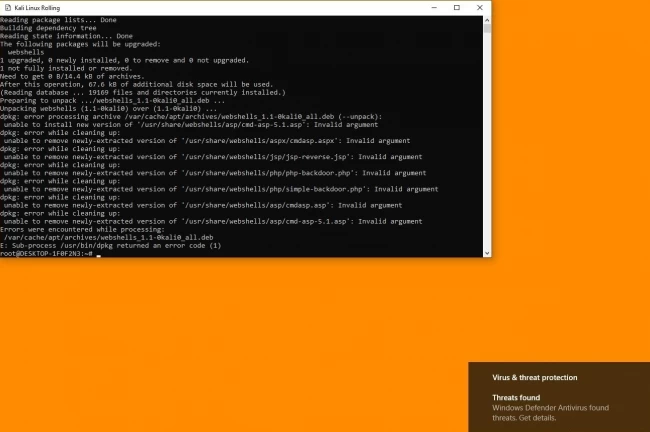
Step 3: After viewing the defender’s message, click on it to open the windows defender page.
Step 4: After opening defender, click on Server and then click on See Details.
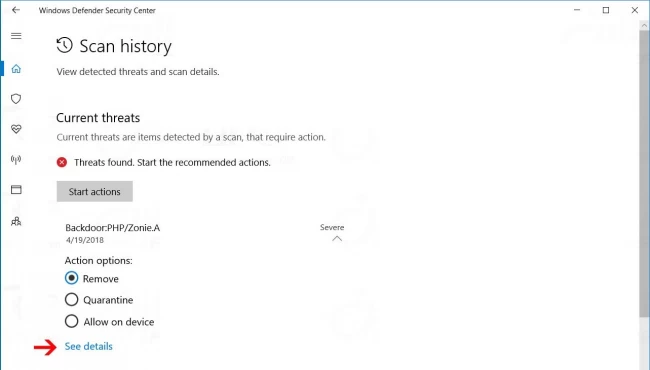
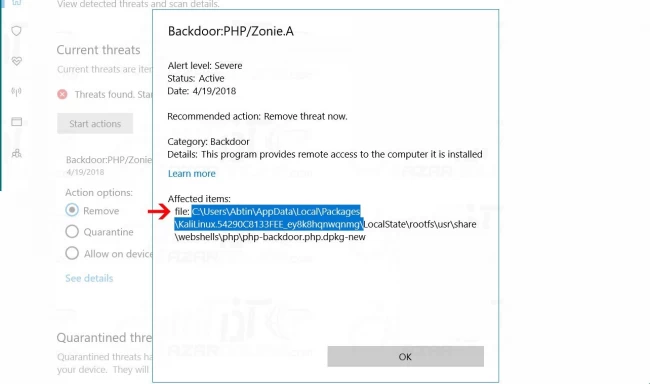
Step 5: Now copy the Kali Linux packages’ installation address (just copy the part which specifies the installation packages’ directory).
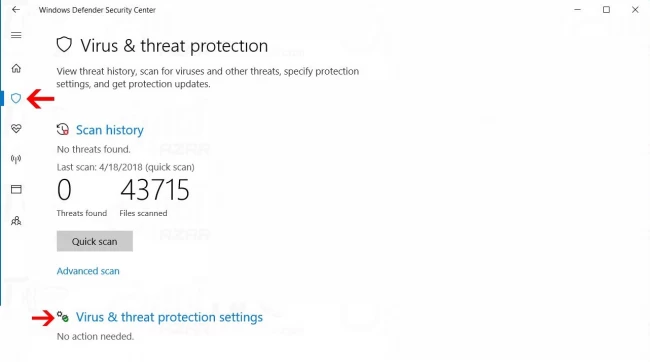
Step 6: On the right side, click on Virus & Threat Protection, then on the opened page, click on Virus & Threat Protection Settings.
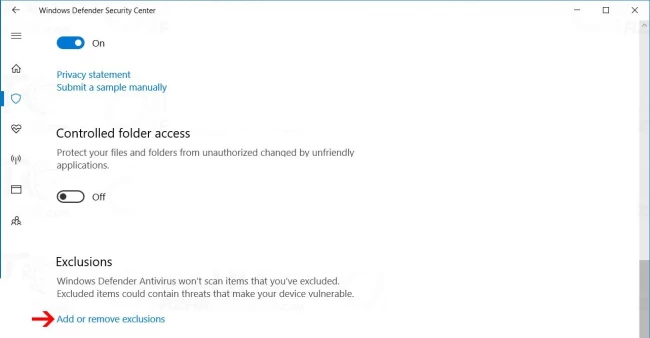
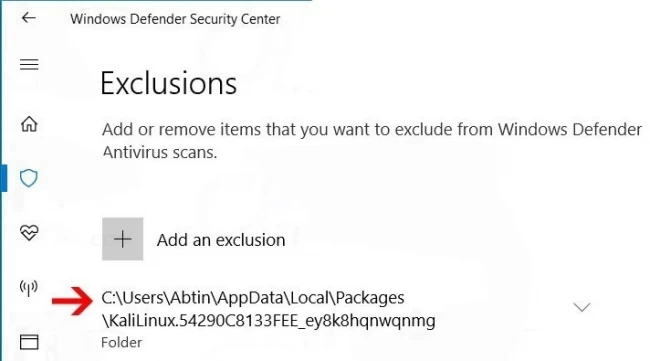
Step 7: In the Exclusions section, click on Add or Remove Exclusions.
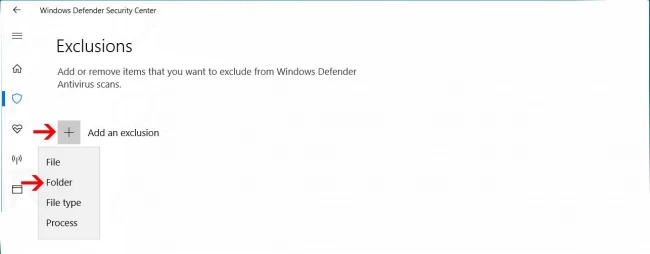
Step 8: On this page, click on Add an Exclusion option and select Folder
Step 9: Paste the directory address which you copied in this section.
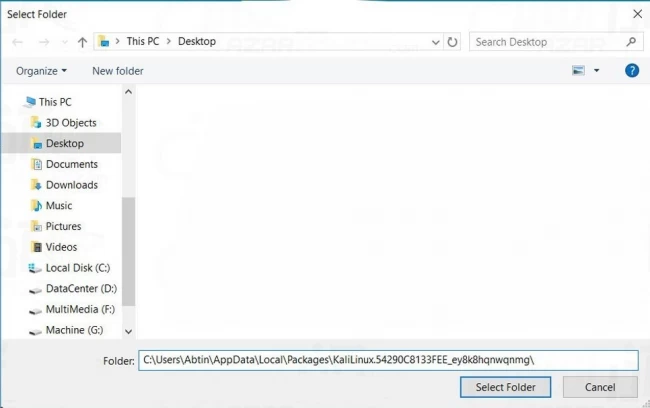
Step 10: After adding this address, you should not have issues with installing Kali packages.
Conclusion
Even if you are not planning to work in IT or Network Security, getting and using a Kali Linux installation is a great way to learn more about networking and common network security vulnerabilities. We hope that this detailed tutorial has helped you to learn more about Kali Linux and successfully install its packages on your operating system. If you have any questions or run into any problems throughout the installation procedure, please leave a comment in the comment section below.
