List of content you will read in this article:
- 1. Understanding Socket Secure Layer
- 2. History of SSL
- 3. How an SSL Works
- 4. Symmetric Key Algorithm
- 5. Public key Algorithm (Asymmetric Key Algorithm)
- 6. What is Message Authentication Code?
- 7. Forward Secrecy
- 8. How to identify an SSL certification?
- 9. Types of SSL Certificates
- 10. Advantages of having an SSL
- 11. Conclusion
There is no secret that the internet is filled with all types of information, so security has become one of the key components to consider. Due to this, most websites on the internet are recommended to provide security for their visitors. In this scenario, SSL certification comes into the picture.

It is strongly advised that all websites on the internet have an SSL certificate. Nowadays, most web browsers show a "not secure" sign on the URL bar for sites without an SSL. The bottom line is that you need an SSL if you want your website to appear legitimate and trustworthy. Specifically, if your website sells some products or services or stores user data, an SSL certificate is required. An SSL can protect your and your users' data. Not only that, but it also has a big effect on ranking well on Google.
Still, many of you wonder: what is SSL certificate, and which one will work with your website? We will go through the different types of SSL certificates so that you can pick the one that suits you best. So in this guide, we will cover thorough information on SSL and TLS and compare SSL vs TLS.
Understanding Socket Secure Layer
SSL, an abbreviation for Secure Socket Layer, is a cryptographic protocol designed to provide network security. These small data files bind a cryptographic key to a company's credentials. However, SSL is no longer being used because TLS, or Transport Layer Security offers more reliable options.
Even though SSL is outdated, we still use the term "SSL" to provide TLS certifications because it's commonly unknown that TLS is SSL's successor. To remove the confusion, TLS is depicted as SSL. This security protocol is used in many applications, such as:
- Web browsing
- Instant messaging
- Voice over IP (VoIP)
Due to security measures, having an SSL certification has become one of the most important things for websites to have. In simple words, when a website gets an SSL certificate, all the communications between its servers and the users are secured.
The primary goal of the TLS protocol is to provide privacy and keep the data accurate and consistent between two (or more) computers. So when secured by the TLS protocol, the connection between the server (monovm.com) and the client (Google Chrome, Firefox) should have at least one of the following properties.
- The connection is secured due to the use of symmetric cryptography, which encrypts the transmitted data. Don't be alarmed, we will go through this later on in the article.
- The identities of the communicators are authenticated using public-key cryptography. It is optional but is generally used from the server-side (movovm.com).
- The connection is reliable because each message transmitted includes a message integrity check that prevents undetected or unauthorized alteration of data during transmission.
- A configured TLS provides "forward secrecy," which ensures that any encryption keys put out in the future will not be used to decrypt any TLS communications from the past.
Many methods are used in exchanging keys, encrypting data, and authenticating the message's integrity. Their collaboration contributes to the establishment of a secure connection.
History of SSL
The current version of the SSL certification protocol is TLS 1.3. TLS was first introduced in 1999 and built on the earlier SSL specifications. The transport layer security protocol dates back to 1986 and has grown extensively through the years. SSL came into play in 1995 when Netscape developed it.
Initially, SSL 1.0 was created but wasn't available to the public due to security measures, and then an improved version of SSL 2.0 was released in 1995. After a year, in 1996, SSL 3.0 was introduced with a complete redesign of the protocol. However, SSL 2.0 and SSL 3.0 were deprecated in 2011 and 2015 due to security issues. The next protocol was TLS 1.0, which came out in 1999. Since then, there have been other versions:
- TLS 1.0 (1999)
- TLS 1.1 (2006)
- TLS 1.2 (2008)
- TLS 1.3(2018)
With time, the protocol developed, and with each new version, the security became stronger and better. The encryptions that have been used were updated so much that it's extremely difficult to crack them by brute force attacks.
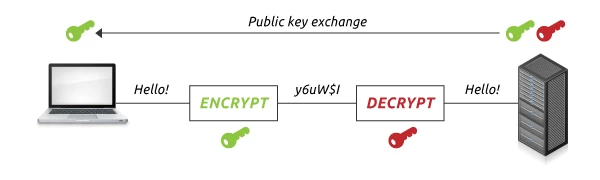
How an SSL Works
In a nutshell, the SSL will encrypt and decrypt data going to and from your website. Let’s talk about the algorithms that are being used to make this happen. SSL certification uses cryptographic technologies like asymmetric and symmetric algorithms, hashes, digital signatures, and message authentication.
Symmetric Key Algorithm
The symmetric key algorithm is a cryptography technology using a single key to encrypt and decrypt text. For this to work, both sender and receiver have to have the same secret key.
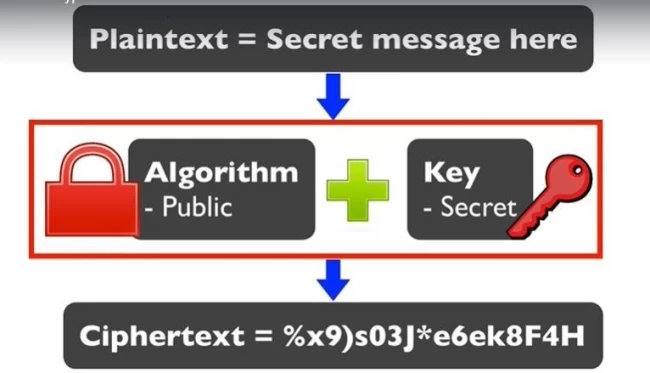
The keys are identical, or there might be a slight difference between the two keys. Thus, only the receiver and sender can encrypt and decrypt the messages going to and from them. The algorithms being used in symmetric encryption are:
- Data Encryption Standard (DES)
- Triple-DES (3DES)
- Blowfish
- RC4
- RC5
- RC6
- Advanced Encryption Standard (AES)
However, giving both parties access to the secret key is one of the main disadvantages of this system compared to public-key encryption (asymmetric encryption).
Public key Algorithm (Asymmetric Key Algorithm)
This encryption method came into existence to tackle the problems with symmetric key algorithms. This system uses a public and private key without having both parties access the same secret key. Instead of having one key (symmetric), they now consider two keys.

- If you encrypt a message with a private key, you will need the public key to decrypt it.
- If you encrypt a message with a public key, you will need the private key to decrypt it.
It is not possible to encrypt and decrypt messages with the same key in this situation. Public keys are available to everyone, while the owner only knows private ones. These are generated by using complex mathematical problems that produce one-way functions. This system means that effective security can be maintained by keeping the private key safe while distributing the public key, which won’t compromise security.
This algorithm is a fundamental security ingredient in modern security systems that assures electronic communications' confidentiality, authenticity, and non-repudiation.
The main algorithms being used for the public-key algorithm are:
- Rivest-Shamir-Adleman (RSA)
- Elliptic curve cryptosystem (ECC)
- Diffie-Hellman (DH)
- El Gamal
What is Message Authentication Code?
For the SSL to function, it uses a message authentication code (MAC) which is sometimes called a tag. It is a short piece of information used to authenticate a message which means it checks if the message has come from the sender and hasn’t been changed. The MAC value protects both the integrity and authenticity of the message.
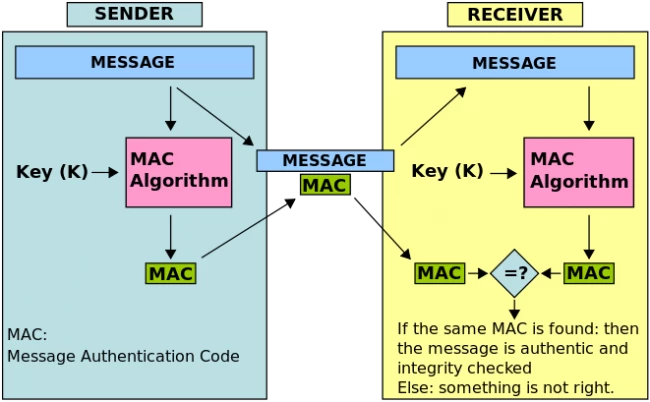
The above image shows how the MAC is being used. When a message is sent from the sender, a MAC key is generated using a key (in this illustration, it's key (k)). Then the message is sent with the authentication code attached to it.
The receiver then runs the MAC algorithm using the same key (key (k)) and compares the two authentication codes. If it's correct, that means the message is authentic and hasn't been tampered with.
Forward Secrecy
Forward secrecy is a special feature of specific key agreement protocols that assure keys will not be compromised even if the private key is compromised. It protects past sessions against the future compromises of secret keys. A new key is generated for every session a user initiates to connect with the website. So even if a key is compromised, it will not affect any future or past sessions.
When using forward secrecy, the encrypted communication sessions, either from the past or the future, cannot be decrypted even if the hacker is actively interfering with the communications (like a man in the middle attack). With a combination of all the types mentioned here and other methods, having an SSL/TLS certification protects your data and privacy. It's like having impenetrable armor on you.
How to identify an SSL certification?
Well, before figuring out how an SSL affects your website, this is how web browsers display a website if it doesn’t have an SSL certification.
![]()
The first thing you will notice is ‘not secure’ in the address bar, which might make visitors want to leave the site. So it’s highly recommended to have an SSL certification because it will not only get rid of the ‘not secure’ sign but also secure the data.
Alright, so back to other visual cues:
The first cue is on the address bar. The website's prefix will be HTTPS:// Here, the additional ‘s’ simply means secure.
![]()
In the address bar, you will see a big indication of safety: a padlock before the web address. This assures that the connection is encrypted and secured.
This assures that the data sent to and from the server and the user will be private and encrypted.
![]()
When used on a website, the Extended Validation SSL Certification (we will talk more about it below) will display the company name in the address bar. This is the most secure form of certification, proving to customers that it’s 100% legitimate.
![]()
As you can see here, there are a couple of visual cues that you can see, and each of these certifications is different.
Types of SSL Certificates
1. Domain Validation SSL Certificates
Domain Validation SSL certificates show that the domain is registered and a site administrator runs the website. Email, DNS, or HTTP can validate this certificate.
When validating via email, the SSL certificate authority will send an email to the site owner, and the site owner will request the certificate. Note that domain-validated certifications provide encryption only. To get one, you must prove the site's owner and get this in a couple of minutes.
These types of SSL certificates are cheaper than the other options. However, there are some downsides. They are not as secure as the other options. Since the verification is only based on the ownership of the domain, a hacker can easily get an SSL. If a potential customer comes to your site, they might hesitate to provide the payment information due to this.
2. Organization Validation SSL Certificates
These types of certificates are similar to getting a DV certificate but with an extra step. In this case, you will verify that you're the website owner and have to verify that you own an organization.
You will need to provide information that proves you're the organization's owner in this country, state, and city. The extra step is to provide the organization's details. Getting the certificate will take a couple of hours to a couple of days. Here's an example of an OV SSL certificate. As you can see here, the organization is validated with domain validation.
3. Extended Validation SSL Certification
It is the most secure certification available out there. To acquire this certification, you will need to provide many more records to prove the company's ownership. This certification provides the same validation as DV and OV certificates. However, it also proves that you have legally registered your company as a business. The validation process takes days or weeks to process the information depending on the certificate authority's requirements. These are granted to companies only if they can prove the following:
- The operational existence
- Location of the company
Due to the number of documents needed for this certificate, this is the most secure type of SSL for validation levels.
|
Factors |
DV SSL |
OV SSL |
EV SSL |
|
Popular among |
Small websites |
Commercial and other websites |
Businesses and organizations |
|
Validation method |
Using an only domain name |
Organization details |
Organizational details and extra documents |
|
CA Approval |
Very Fast |
Fast |
It takes time to verify |
|
Trust |
Average |
High |
Extremely High |
|
Issued to |
Everyone |
Everyone |
Only to businesses and registered organizations. |
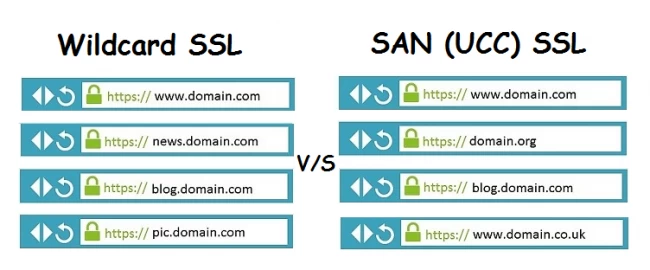
4. Wildcard SSL certification
When getting an SSL certificate, you have to provide a list of subdomains that are also secured. If you use the certificate for a subdomain that isn’t on the list, the ‘not secure’ warning will come. To grasp the idea of wildcard SSL, we should first know what single-name SSL is. Single-name SSL certificates (as the name says) protect one subdomain.
For example, if you purchase a certificate for www.dog.com, it will not apply to account.dog.com. So with a wildcard SSL certification, the above problem is solved. Assume you bought a wildcard SSL for www.site.com, then it will also secure example.site.com.
5. SAN SSL Certification
SAN (Subject Alternative Name) SSL is another term used for multi-domain SSL. This type of certification lets the site owner secure multiple domains and subdomains under a single certificate. With multi-domain SSL certificates, you can combine many different hostnames, regardless of whether they are from the same domain or not. Again, the best way to explain this is through an example. Imagine you have the following domains:
- pqr.com
- pqr.net
- pqr.org
With just one SAN SSL certificate, all these websites will be secured.
Advantages of having an SSL
There are many advantages of having an SSL; the biggest part is that all the data coming to and from the site is encrypted. It means that all the card details, usernames, and data are given to a site are safe from hackers.
Another pillar of having an SSL is that the site is verified. It proves that the site is legitimate and not fake. Many people fall for scams (like phishing scams) where they provide information to fake sites.
Another compelling reason would be that Google likes HTTPS sites, so the sites equipped with an SSL are ranked better.
Conclusion
We hope that this was a complete and informative blog on SSL and TLS and how they are different from each other. Also, a comparison chart between TLS and SSL is included, as we have included all of the requirements around these certifications. SSL certification is important for any website because it helps maintain integrity and security.
People are also reading:

I'm fascinated by the IT world and how the 1's and 0's work. While I venture into the world of Technology, I try to share what I know in the simplest way with you. Not a fan of coffee, a travel addict, and a self-accredited 'master chef'.