List of content you will read in this article:
So, you got yourself a remote server and wish to access it. Well, there are multiple ways you could do so. If it is a Windows server, the most common way you would remotely control it is through Microsoft’s proprietary remote desktop protocol. however, If you have opted for the more widely used Linux operating system on your server, this option is not available. Instead, you would use Telnet or SSH to access a remote server, the latter being the better option. This tutorial will help you to understand the comparison between Telnet vs SSH Protocols, their advantages, disadvantages, and differences between them. In the last, we will discuss some advice on which protocol you should pick when accessing a remote server.
Difference Between Telnet and SSH
Both Telnet and Secure Shell (i.e. SSH) are network protocols used to connect to remote servers and both have been used widely at different points in time. Telnet is the original protocol that was used when the internet was first launched in 1969. It was developed to be used in private networks and has no security measures, making it irrelevant when used on public networks. This is the main reason why SSH was developed as a replacement for Telnet. We will discuss the differences between telnet and SSH, however, let's first understand what each one is.
What is TELNET? [Definition]
Telnet is a remote protocol that allows a user to communicate with a remote device. It is an abbreviation for Terminal Network, Telecommunication Network, or Teletype network, depending on the source. It was originally built to be a form of remote control to manage mainframe computers from distant terminals. Telnet is a text-based computer protocol, meaning it does not contain a GUI (i.e. Graphical User Interface). here we have listed some of the best features of the TELNET protocol.
Features of TELNET
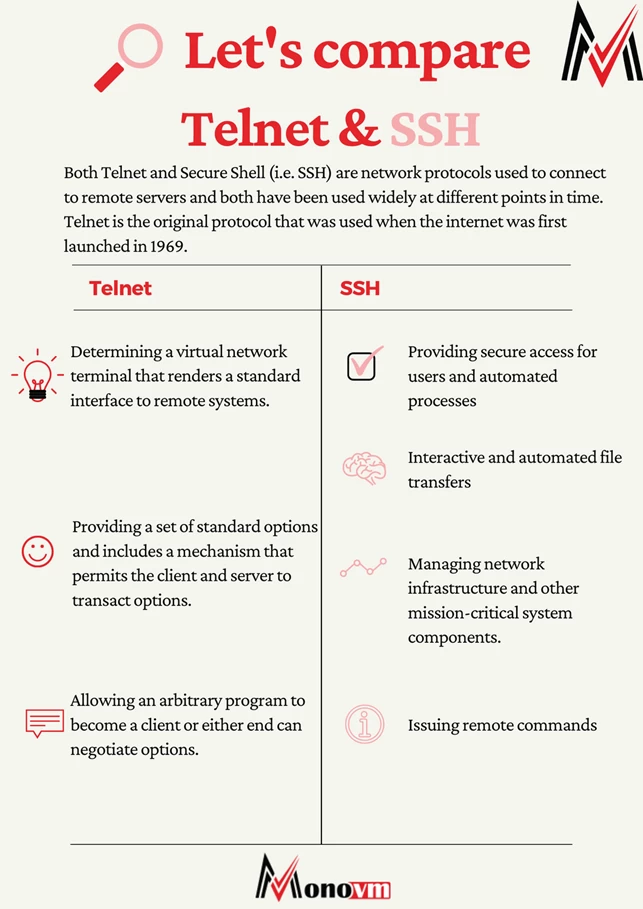
- Determining a virtual network terminal that renders a standard interface to remote systems.
- Providing a set of standard options and includes a mechanism that permits the client and server to transact options.
- Allowing an arbitrary program to become a client or either end can negotiate options.
Due to the lack of security measures, Telnet has been almost completely replaced by SSH in nearly all usage scenarios.
Advantages of TELNET
- This protocol can be used to send and receive information.
- Supports user authentication.
- The collaboration of multiple users
- You can use it to send and receive information.
- This remote login saved your research hours.
- There are no authentication policies & data encryption techniques used in Telnet, causing a huge security threat.
Disadvantages of TELNET
- Telnet is not an Ideal Protocol to transmit cursor movements or GUI information.
- Does not support the transport of encrypted data. Instead, it only supports known port numbers.
- Dynamic port not supported.
- Telnet does not encrypt any data sent over the connection.
- Port numbers can be exploited.
- Display only text and numbers, no graphics and color.
What is SSH? [Definition]
Secure Shell is a network protocol that gives users a secure way to access a computer over an unsecured network. It provides several alternative options for strong authentication, and it protects the communication's security and integrity with strong encryption. Unlike Telnet, once an SSH connection is established, the data that is transmitted is encrypted according to the parameters negotiated in the setup in accordance with industry-standard strong encryption algorithms (e.g. Advanced Encryption Standard). During this stage, the client and the server both agree on the symmetric encryption algorithm to be used and generate the encryption key. The typical uses of the SSH protocol:
Uses Of SSH Protocol
- Providing secure access for users and automated processes
- Interactive and automated file transfers
- Issuing remote commands
- Managing network infrastructure and other mission-critical system components.
Advantages of SSH
- It is available free for non-commercial use.
- The open-source version has gone through improvements like bug fixes, patches, and offers many additional functionalities.
- SSH may offer multiple services using the same connection.
- SSH helps you to securely tunnel insecure applications like SMTP, IMAP, POP3, and CVS.
- The tunneling of ports works effectively for simple VPNs.
- It offers strong authentication and secure communications over insecure channels.
- SSH allows users to log into another computer over an insecure network securely.
- Provide privacy of your data via strong encryption.
- The integrity of communications is performed in such a way that it cannot be altered.
- Authenticate proof of identity of senders and receivers.
- Allows you to back or forward or to encrypt other TCP/IP- based sessions.
- Allows the user to view the contents of directories, edit files, and access custom database applications remotely.
Disadvantages of SSH
- SSH connection does not allow you to run GUI tools.
- It is not designed to transmit cursor movements or GUI movement information.
- It is not a secure protocol.
- SSH protocol is not able to fix all TCP's problems since TCP runs below SSH.
- SSH cannot protect users from attacks made through other protocols.
- This protocol does not protect Trojan horses or viruses.
TELNET vs SSH: Head to Head Comparison
Through this infographic, you will get to know a detailed comparison between ssh vs telnet and know which protocol to choose.
Even though both protocols serve the same purpose, Telnet is a conventional protocol whereas SSH is the replacement for Telnet, also providing some enhanced features.
Telnet transmits all data in plain text format (yes, even passwords), allowing for anyone on the network to be able to intercept the traffic and effortlessly access it. As one can imagine, this is a tremendous security risk and is the primary reason why Telnet is nearly extinct today.
on the other hand, SSH uses encryption for all transmitted layers, making security breaches less likely to occur and allowing it to withstand eavesdropping, man-in-the-middle, and insertion/replay attacks.
Here is a guide on how you can connect to a Linux VPS server with SSH.
Conclusion
While both Telnet and SSH can be used to transmit data to remote servers, it is not only highly recommended to use the latter, but also has become a standard industry practice to do so. Nevertheless, we are not here to instruct you on what to do, thus we explained both network protocols and listed their upsides & shortcomings. Instead, we are here to inform you to the best of our abilities on which one will be more useful to you. this is all about the detailed comparison between telnet vs ssh protocols so you can choose the best one to increase our productivity, if you think there are other differences that might be helpful to choose the one you can comment via the below-listed comment box.
People Are Also Reading:
