List of content you will read in this article:
SQL injection is the most prevalent web security vulnerability that allows the hacker to manipulate malicious SQL statements. They control a database server behind the website's main interface. Behind every single web, an application database plays a crucial role that determines the actual security and vulnerability of a website.
It usually allows a criminal hacker to view data that are not generally accessible. This database might include data belonging to other users, IDs, passwords, and the rest of the media files uploaded on the website's database. Attackers use SQL injection vulnerabilities to jump over the application security measures.
Criminal attackers can access authentication and authorization of a web page and web application and hijack the entire SQL database's content. As we discussed, they can access media files and password kinds of stuff, but they can also use SQL injection to modify, add and delete data in the database.
An SQL Injection vulnerability can badly affect any website or web application that uses an SQL database. These databases include MySQL, Oracle, SQL Server, or many others. The main motive behind by-passing the security barrier of SQL is to gain unauthorized access to your sensitive data.
Sensible data means your customer's information, personal data, intellectual property, trade secrets, and many more. SQL injection attacks are one of the most dangerous and prevalent attacks in the world. SQL injection vulnerability comes under the top 10 as the higher number of threats to web application security in the OWASP organization's list. In many situations, hackers can hijack an SQL injection attack to arbitrate the underlying server or back-end database.
How and Why Is an SQL Injection Attack Performed?
The process of finding or accessing the website's database using SQL injection comes with finding vulnerable user inputs within the web pages. Any web application or web page that consists of SQL Injection vulnerability uses random information directly in an SQL query. The hackers usually create input content, and this content is often thought to be a malicious payload. It is the number one part of the attack. Afterwards, the hackers transfer the content, which means malicious SQL commands are executed in the database. By doing these actions, they play with the database's logical structure and manipulate it to by-pass the verification procedure.
SQL is considered to be a query language that was developed to manage data stored in relational databases. Website owners or even hackers can use it to access, modify and delete data. A large number of websites store all the data in SQL databases. In various cases, you can quickly use SQL commands to perform operation system commands. Thus, the right SQL Injection attack can have severe results.
- Hackers can use SQL Injection to search the credentials and details of other users from the database. They can even impersonate their users. The emulated users can be considered as the database administrator that has all the database rights.
- SQL gives you control to select and out data from the database. A significant number of changes that SQL Injection vulnerability could allow the hackers to gain full access to all data on your database server.
- SQL also grants you to alter data in a database and modify or add some new data. For instance, in a financial application, a hacker could use SQL Injection to limit balances, transfer money to their bank accounts, and break the entire organization's capital.
- You can even use SQL to eliminate records from a database and sink tables. Suppose the administrator tries to back up the hijacked database, yet deleting data will affect application availability. However, there have been many cases where backups do not cover at all.
- You can intentionally or accidentally gain access to the operating system using the database server in a few database servers. In these cases, hackers can use SQL Injection as the original vector and further attack the private network behind a firewall.
Simple SQL Injection Example
The first example is very easy. It displays how hackers can use an SQL injection vulnerability that we discussed above. They use SQL Injection vulnerability to by-pass the security layers and access authenticates as the administrator. The following example is pseudocode executed on a web server. It is by far this simplest example of authenticating with a username and a password. The example database has a table where you can see the names in the columns.
|
# Define POST variables uname = request.POST['username'] passwd = request.POST['password'] # SQL query vulnerable to SQLi sql = “SELECT id FROM users WHERE username=’” + uname + “’ AND password=’” + passwd + “’” # Execute the SQL statement database.execute(sql) |
The place where they input the details is vulnerable to SQL Injection. A hacker can use SQL commands in such a way that will alter the SQL statement administered by the database server. For instance, they could use some tricks and technique that involves a single number and set the password:
|
password' OR 1=1 |
Afterwards, the database server will be performing according to this SQL query:
|
SELECT id FROM users WHERE username='username' AND password='password' OR 1=1' |
Due to the OR 1=1 statement, the WHERE condition will return the first id from the user's table irrespective of the actual username and passwords. The administrator is the first user id in a database.
By following this pattern, the hacker will be able to by-pass authentication and access the administrator perquisites. These hacks can also illustrate the rest of the SQL statement to repress the SQL query's accomplishment.
|
-- MySQL, MSSQL, Oracle, PostgreSQL, SQLite ' OR '1'='1' -- ' OR '1'='1' /* -- MySQL ' OR '1'='1' # -- Access (using null characters) ' OR '1'='1' %00 ' OR '1'='1' %16 |
Example of a Union-Based SQL Injection
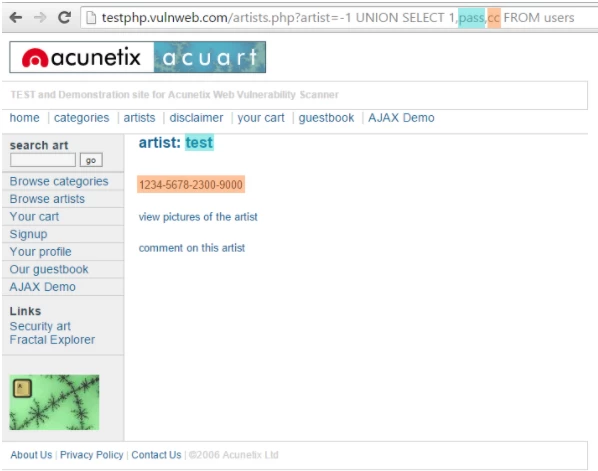
It is one of the most common types of SQL Injection where a hacker uses the UNION operator. This method allows the hacker to join the results of two or more SELECT statements into a single result. This technique is called union-based SQL Injection. The following script is an example of this technique. The process complies with the web page testphp.vulnweb.com, a purposely unprotected website hosted by Acunetix. The following HTTP requires a standard request that a general user would probably send.
|
GET http://testphp.vulnweb.com/artists.php?artist=1 HTTP/1.1 Host: testphp.vulnweb.com |
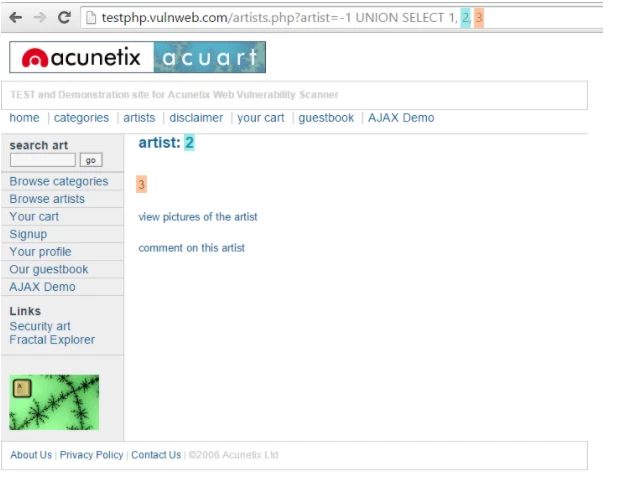
The artist is unprotected from SQL Injection. Besides, the payload adjusts the inquiry to search for an inexistent record. It creates the values in the URL query chain to -1. It could be any other value that does not become available in the database. A negative value is good to guess because an identifier in the database is unusually a negative number.
In SQL Injection, the Union operator is ordinarily used to associate a malicious SQL condition to the origin query proposed by the web application. The effect of the entered query will be matched with the result of the original query. It allows the hacker to retrieve column values from the other tables.
|
GET http://testphp.vulnweb.com/artists.php?artist=-1 UNION SELECT 1,pass,cc FROM users WHERE uname='test' HTTP/1.1 Host: testphp.vulnweb.com |
|
GET http://testphp.vulnweb.com/artists.php?artist=-1 UNION SELECT 1,pass,cc FROM users WHERE uname='test' HTTP/1.1 Host: testphp.vulnweb.com |
How to Prevent an SQL Injection
One of the most trusted ways to prevent SQL Injection attacks is input validation and parameterized condition. Also including adjusted statements. The application scripts should never be used to input directly. Programmers will have to sanitize all input, not only web form inputs like login forms. They have to remove potential malicious code and elements such as single quotes. Another good idea is to turn off the distinctness of database errors on our production sites.
Keep in mind and database errors can be quoted with SQL Injection to retrieve information about your database. If you find any SQL Injection vulnerability, for instance, using an Acunetix scan, you may not be able to fix it immediately. Another example could be, let's assume, the vulnerability may be in open source code.
In these cases, you must use a web application firewall to protect your input momentarily. If you want to learn how you can prevent SQL Injection attacks in the PHP language, check out our blog to fix them.
Another significant thing everyone must consider doing is guiding through Bobby Tables. Means to learn "how can you prevent SQL Injection vulnerability from other programming languages from SQL Injection. Furthermore, you get even more ideas of how you can protect your server from SQL Injection vulnerability down below.
How to Prevent SQL Injections (SQLi) – Generic Tips
The first thing to keep in mind is preventing SQL Injection vulnerabilities is no piece of cake. The solution for several SQL Injection vulnerabilities applies specific prevention techniques that depend on the subtype of SQLi exposure. The same applies to the SQL database engine and the programming languages.
However, there are several typical strategic sources that you must follow to keep your web application safe from precious hacks. Some of this statement can be considered as effective SQL prevention methods.
Step 1: Training & Awareness of SQL Infections
In the process of keeping your web applicator safe, everyone who is involved in developing the web application must be aware of the risks associated with SQL Injections. A firm security training is required for all the IT staff and developers of the company. Some of the prominent developer positions that should intensely focus on SQL Injection are QA staff, DevOps, and SysAdmins. You can also share this post where we talked about all the consequences of SQL Injection.
Step 2: Don't Trust Any User Input
Input is a term that imports data into a database table from an external source or import from a generic data source—similarly, any information or data sent to a computer for processing is considered input. To prevent potential SQL Injection vulnerability, every developer should treat all user input as an untrusted source.
Another thing to keep in mind is that any user input held in the SQL query increases the risk of SQL Injection. It would help if you handled internal uses the same way you treat the standard input. Another point to notice is that validation should not only apply to the field but also allows users to type in the information.
It would help if you considered using regular expressions as whitelists for structured data includes age, income, name, zip code, etc. For the case of a fixed set of values such as the radio button, drop-down list, determine the correct value being treated. Keep in mind the input data should match a few of the offered options directly.
Step 3: Use Whitelists, Not Blacklists
Whitelists are considered to be a cybersecurity list. It means only giving administrator-approved programs, and IP and email addresses, system access. Whitelists are not as fit all sizes in one place. Instead, administrators tailor creates whitelists based on their unique requirement. On the other hand, many reasons and a defense that many developers face with the blacklist are so many.
They cannot block significant keywords on the blacklist. Perhaps the biggest problem with blacklists is they can stop people from performing legal requests. It would create multiple confusion for legitimate requests and unethical requests together. However, you must use whitelists, not blacklists, and don't filter user input toward blacklists. Hackers are always finding a way to by-pass your blacklist. We recommend, verify and filter user input using strict whitelists singularly.
Step 4: Adopt the Latest Technologies
Did you know that old web development technologies lack SQL Injection support? Therefore, every little organization should adopt the latest version of the development system, language. Besides, it is even more crucial to be updated with the latest technologies associated with the environment. There have been many cases where databases couldn't restore due to robust SQL Injection issues. Some of the top examples we have PHP use PDO instead of MySQLi.
Step 5: Employ Verified Mechanisms
It would be best if you took a smart leap toward preventing SQL Injection. Due to its terrifying popularity, modern development technologies nowadays offer an intelligent mechanism to protect against SQL Injection vulnerability. Don't try to build SQL Injection protection by yourself and use tools to replace this occurrence.
For example, you can use stored producer or parameterized queries. The SQL server will maintain only one execution plan in its plan cache by adopting a parameterized query and uses it multiple times for specific values applied to this state. It is very similar to a stored procedure. The parameterized query process is pretty economical due to its performance and resource utilization ability.
Step 6: Scan Regularly with Acunetix
Security scan is an automatic process that scans part of an application, network, or device to check for security errors. Security scanning comes with huge advantages. It is something that should be tackled every single time to review the information remains secure. SQL Injection awareness is spreading all of the development community.
There are levels of security scanning. One of the best ones is a web application vulnerability scan. It checks web applications for any vulnerabilities that would probably allow attackers to gain aces. Did you know there are several types of openness, and the most one is SQL Injection? Therefore, you must regularly scan your web application using a web vulnerability scanner. Always consider using Acunetix.
Conclusion
Web development technology is coming up with the latest prevention methods to protect from SQL Injection. We talked about many steps and directions to prevent the data from getting exposed in the hacker community. A database is the only weapon behind every single website and the source for maintaining the full environment.
If anyone leaves the idea of protecting their data from "cyber threats and SQLi," they will have to go through several steps to retrieve their information. Sometimes it's almost impossible to get your data back. While many claim it, all can be recovered, but the primary sources will endorse vulnerability.
We also showed you how you could try using scripts to manipulate the other server using "union-based SQL Injection" & simple SQL Injection Example. Furthermore, to prevent SQL Injection, we displayed generic tips that can help anyone be more aware. All directions are curated with immense effort to prevent the spread of SQL Injections. Bear in mind, and you must utilize the latest and robust web development technologies & full security layer to protect your database better.