List of content you will read in this article:
We are living in a digital era today. Everything is becoming digital. From booking concert tickets to paying money – all tasks can be performed online. While such convenience has led to our increased pleasure, it has invited some problems as well. One such problem is DDoS attacks. In fact, it is among the most rampant security issues in the digital realm today. Here, we will discuss the reality of DDoS attacks and how one can terminate their chances for good. Let’s find out.
What is a DDoS attack?
Distributed denial-of-service attacks or DDoS attacks are among the topmost internet safety concerns ever. This type of attack seeks to hamper the usual traffic of a victim. That is a server/network/service. Such attacks achieve their aim by submerging their targeted prey with a huge amount of network traffic.
These attacks try to become effective by using a plethora of PC systems as the attack sources. These include many exploited machine types such as desktops and even other networked resources like the Internet of things devices.
To put it simply, a DDoS attack has a similarity with an undesired traffic jam blocking a particular road and as a result, blocking the path of the normal traffic to reach their destinations.
How does a DDoS attack work?
A DDoS attack can only take place with the help of networks of machines connected to the internet. These types of attacks can never occur offline.
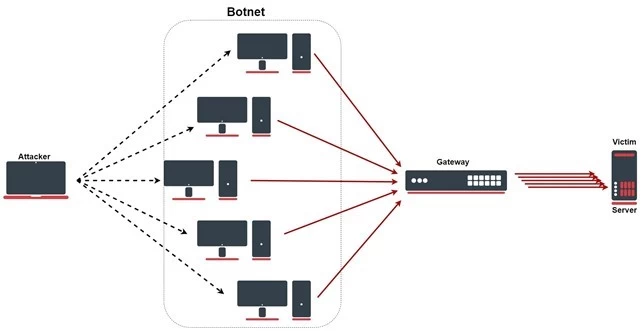
The network we’re talking about comprises PCs and other network devices, for example, IoT devices. But for such an attack to happen the attacker must infect these machines with malware so that they can control them sitting far away. Such infected machines are referred to as bots. And, groups of such bots are known as botnets.
Once the attacker has been capable of constructing a botnet, they can initiate the attack by giving instructions remotely to each of the bots.
When a specific server or network becomes the aim of the attack by a botnet, two things happen. First, each bot within that botnet starts sending requests to the prey’s IP address which causes the server/network to become submerged in internet traffic. And, second, the target faces a denial-of-service to usual traffic.
As each one of these bots is a legit machine, it becomes quite difficult to isolate the attack traffic from the usual one.
Network connections on the internet comprise different layers of the OSI Model and different DDoS attacks focus on particular layers. For example:
- Layer 3, Network Layer. Attacks are known as ICMP floods, Smurf Attacks and IP/ICMP fragmentation
- Layer 4, the Transport layer. Attacks include SYN Floods, UDP Floods, and TCP Connection Exhaustion.
- Layer 7, the Application layer. Mainly, HTTP-encrypted attacks.
DDoS attack types
As we already said, a DDoS attack gets launched from devices that have been compromised, also known as botnets. Broadly speaking, we can divide such attacks into three distinct categories:
Application Layer attack
Layer 7 DDoS attacks mainly focus on exhausting the resources of the target. The attack takes place where the web pages are generated on the server and are delivered as HTTP requests. This is difficult to defend as the traffic is difficult to be considered malicious. Usually when a request is made the server often loads multiple files and run database queries in order to create a web page but when there are multiple requests the exhaustion of resources takes place.
HTTP Flood: This is similar to pressing refresh in a web browser over and over from many different computers at once resulting in a large number of HTTP requests flood the server and causing a denial-of-service.
Protocol Attack
Protocol attacks use the weaknesses in layer 3 and layer 4 of the OSI model and make the target inaccessible. These attacks consume all the available state table capacity of web application servers or intermediate resources like firewalls which causes a service disruption.
SYN Flood: This attack exploits the TCP handshake by sending a target a high number of “Initial Connection Request” SYN packets with spoofed source IP addresses. The target machine responds to all the connection requests and waits for the final step of the handshake which never occur which in turn exhausts the target’s resources.
Volumetric Attacks
Consuming all available bandwidth by creating congestion between the target and the internet falls under this category of attacks. Large amounts of data are sent to a target by using a form of amplification or other methods which create massive traffic such as requests from a botnet.

DNS amplification: A request is made to an open DNS server with a spoofed IP address and then the target IP address receives a response from the server. The hacker structures the request such that the response from the DNS server to the target will contain large amounts of data. As a result, the target receives an amplified amount of data that of the initial request from the attacker.
Apart from these three main types of attacks, there are zero-day or zero-minute exploits. These types of attacks are an umbrella for all new or unfamiliar DDoS attacks. Such attacks are extremely harmful as we have no patches available that can get rid of them. This term is a hot topic among the hacker community today and they are trying to discover, exploit, and exchange new zero-day vulnerabilities.
The motives behind the DDoS attacks
With each passing year, these DDoS attacks are becoming more rampant. They have become a huge concern for the cybercrime departments across the world. A visible trend among all such attacks is a shorter attack span yet a larger PPS attack volume. These types of attacks happen as a consequence of some of the following motives:
The digital realm is filled with self-proclaimed hacktivists. These people utilize such attacks as a weapon of their choice to attack those sites with which they have major ideological differences.
Next, we have boredom. Cyber vandals love to launch a DDoS attack whenever they feel bored. In fact, they have no specific motive behind such attacks. They do such stuff just for the fun of it and get some much-needed adrenaline rush.
Often the motive behind such attacks is business feuds. Many businesses around the world hire people to perpetrate such attacks to get rid of their rival organization’s website, stopping them from participating in many important events like the famous Cyber Monday. Doing so helps them to gain the upper hand in several business aspects.
DDoS attacks are also utilized for extortion from victims. Many cybercriminals tend to use these attacks or threaten to attack a target for making a great sum of money fast.
Such attacks are also common phenomena in cyber warfare. Many Government-backed DDoS attacks are utilized both to batter the enemy government’s significant websites as well the infrastructure of their nation.
How can one recognize a DDoS attack?
There are many proven ways to recognize a DDoS attack after it’s been initiated. The simplest and most obvious among them is when your website or network becomes slow or unreachable out of nowhere. However, this symptom could also give rise to confusion as a genuine traffic surge may also be the cause of such a slowdown. Hence, before ascertaining that you’re indeed facing a DDoS attack, you have to perform some further examination. Traffic analytics tools can aid you in spotting some of the more concrete symptoms of a DDoS attack. Here are some of those symptoms:
- An incredulous amount of traffic coming from a solo IP address or range.
- Lots of internet traffic comes from users sharing a sole behavioural profile. This could be a device type, location, etc.
- A questionable boost in requests to a particular page.
- Unusual traffic patterns happening at unusual times of the day.
How can one resist such DDoS attacks?
The main thing you have to figure out while planning your resistance against DDoS attacks is to differentiate between the usual traffic and the attack traffic.
After you’re done identifying what is what, it’s time to take action. Here are some ways for preventing all three types of such attacks:
For volume-based DDoS attacks, it’s best to try to soak them up with a global network that has scrubbing centers. Doing so will help in scaling that can prevent such attacks.
Now, for protocol attacks, try blocking the crooked traffic before it reaches its destination. That is your site. By utilizing technologies that help identify visitor IDs can resist these protocol attacks. Such technologies are capable of easily and effectively differentiating between authentic site visitors such as humans and mechanized and harmful clients.
Lastly, we have the application layer attacks. For such attacks, you can opt for tracking the behaviour of your site visitors, blocking bots that you know are malicious, etc. You can also make an assessment of the clients that you don’t recognize or feel are incredulous. For doing so, you can take the help of online JavaScript tests, cookie tests, or even the classic CAPTCHA.
Application front-end hardware
These are intelligent hardware placed on the network before any traffic reaches the servers. They analyze the data packets as they enter the system and organizes them as a priority, regular or dangerous. These are used on networks integrated with routers and switches.
Blackholing and Sinkholing
Blackholing is when all the traffic attacking a specific IP is redirected to a non-existing server aka a black hole. This will be more efficient and to avoid network connectivity it can be managed by the ISP.
Sinkholing is not efficient for most severe attacks because in sinkholing the traffic is sent to a valid IP address which analyzes and rejects the bad packets.
Upstream Filtering
Before entering the server all traffic is passed through a “cleaning center” or “a scrubbing center” through different methods like proxies, tunnels or digital cross connectors which filters bad traffic (DDoS and other common internet attacks) and passes through only the good traffic. In this method, the provider needs to have central connectivity to the internet in order to manage this kind of service.
DDS based defence
A DoS defence system (DDS) can block connection-based DoS attacks and legitimate content but with bad intentions. A DDS can protect against both protocol attacks (ping of death and teardrop) and rate-based attacks (ICMP floods ad SYN floods).
Firewalls
In the case of a simple attack, it is possible to deny all the incoming traffic from attackers based on protocols, ports, or the origination IP address. But more complex attacks will be hard to block with simple rules.
Conclusion
As you can see, DDoS attacks are among the leading causes of the headaches of cyber cells from all over the world. The motives behind such malicious attacks are manifold. Be it just for fun, taking down a rival website, or engaging in cyber warfare – these types of attacks are becoming more rampant in today’s world.
So, if you own a website, it can also suffer from such an attack. Perhaps someone out there would love to see you suffer. So, the best thing you can opt for is to educate yourself of these attacks, their motives, types, and so on. Doing so will help you understand the magnitude of what you’re in for. But that won’t suffice alone. You got to know how to mitigate these attacks as well.
Luckily, our article discusses both these aspects as well as the whole nine yards of DDoS attacks. Refer to it and you should have no problem protecting your PC from suffering any such attacks. Here, we gave you the possible preventions for each variety of these attacks. Understand first what can cause your misery, and then, take necessary precautions to avoid them. Good luck!

I'm fascinated by the IT world and how the 1's and 0's work. While I venture into the world of Technology, I try to share what I know in the simplest way with you. Not a fan of coffee, a travel addict, and a self-accredited 'master chef'.